 St. Clair Intellectual Prop. Consultants v. Cannon, 2009-1052 (Fed. Cir. 2011) [PDF]
St. Clair Intellectual Prop. Consultants v. Cannon, 2009-1052 (Fed. Cir. 2011) [PDF]
This case raised the issue of whether one or two references to an alternative embodiment (MPEG) in the specification can overcome the predominance and repeated reference to the first embodiment (still images). Two issues are explored here (1) whether all the claims were limited to an interpretation requiring the infringing devices to have formats corresponding to different computer architectures, and (2) whether the claim language of “plurality of different data formats” includes moving (movie) images or only still images. The district court found infringement, the appeals court disagreed and reversed, with one judge dissenting.
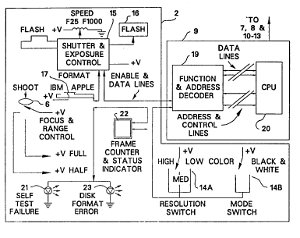
In St. Clair the plaintiff sued several digital camera manufacturers for infringing United States Patent Nos. 5,138,459 (“‘459 patent”), 6,094,219 (“‘219 patent”), 6,233,010 (“‘010 patent”), and 6,323,899 (“‘899 patent”). Claim 16 of the ‘459 patent provides: “A process for storing an electronically sensed video image comprising the steps of: . . . recording in selectable addressible memory means at least one of a plurality of different digital output data format codes where each of said plurality of out-put data format codes corresponds respectively to one of a like plurality of different data formats for different types of computer apparatus.”
The parties disputed whether the phrase “plurality of different data formats for different types of computer apparatus” language” was limited to formats related to different computer architectures (e.g., IBM or Apple PCs) or if it could also include formats related to different computer applications (e.g., software that can run GIFF or PICT). If the phase was limited to different computer architectures then Fuji, the appellant, would avoid infringement.
Majority: Claims Treated Similarly Requiring Different Computer Architectures. Reviewing the specification and the prosecution history, the majority found that the claim phrases should be limited to the different computer architectures and not the broader interpretation of formats related to different computer applications. During the prosecution the inventors stated, as summarized by the court, that the invention ” ‘solve[d] a long felt need’ by allowing data format compatibility with a ‘plurality of types of personal computers manufactured by different [personal com-puter] companies, IBM PC, Apple, Sun Micro Systems, Digital Equipment, etc.’ ”
Dissent: Not All Claims Contain Architecture Language and Deserve Broader Interpretation. Some The dissent agreed with the majority regarding claims having the language of “a plurality of different file formats for different types of computer apparatus” or “a plurality of different data formats for different types of information handling systems.”  However, the dissent asserted that the claims of the ‘010 and ‘899 patents did not contain the “for different types of computer apparatus” limitation. For example, claim 1 of the ‘010 patent provides “…a digital control unit for formatting said digital image signal in one of a plurality of computer formats.” The dissent asserted “Because the inventors omitted the ‘for different types of computer apparatus’ limitation, the plain language of those claims is broader.” Further the dissent found that neither the specification nor the prosecution history supported importing such a limitation into those claims. The dissent would have affirmed the district courts finding of infringement.
Majority: Use of “Still” and “Image” throughout Patents Excludes Video Coverage. The majority found the repeated use of the word “still” in the title and the abstract of the ‘459 and ‘219 patents, and its use throughout the specification and summary of invention of all of the patents precluded the possibility that the “plurality of data formats” limitation in claim 16 included moving image formats. The majority noted that the word movie did not appear anywhere in the patents. A finding that this limitation covered movie formats would have resulting in infringement.
Dissent: Single Reference to MPEG and DVI is Sufficient to Broaden Claim to Cover Video. The disent noted that the specification expressly names MPEG and DVI compression as “an alternative embodiment of the present invention.” ‘459 patent col.10 ll.46-59. It is known that MPEG and DVI are video formats. The dissent found that the claim language of “plurality of different data formats” plainly included MPEG video and thereby video formats. Again the dissent’s interpretation would have resulted in affirmation of the district courts finding of infringement.


 Today, the Silicon Prairie Social organizers announced their
Today, the Silicon Prairie Social organizers announced their